Sudo allows system administrators to allow users run command as root user. The commands that run with sudo needs to be logged in for security and compliance reasons.
Security — Sudo logs can provide a trail of activity. Any unauthorised access or suspicious behaviour can be logged and the system admins can get to know with the help of sudo logs.
Compliance — Sudo logs are required for regulatory requirements for an organisation. HIPPA, PCI, DSS provide system activity trail.
Accountability — It documents the actions when administrator perform, system admin tasks.
We can create a custom sudo logs file in /etc/sudoers
/etc/sudoers is a configuration file used by the sudo command in Linux and Unix-based operating systems. It contains the rules that determine which users or groups are allowed to run specific commands.
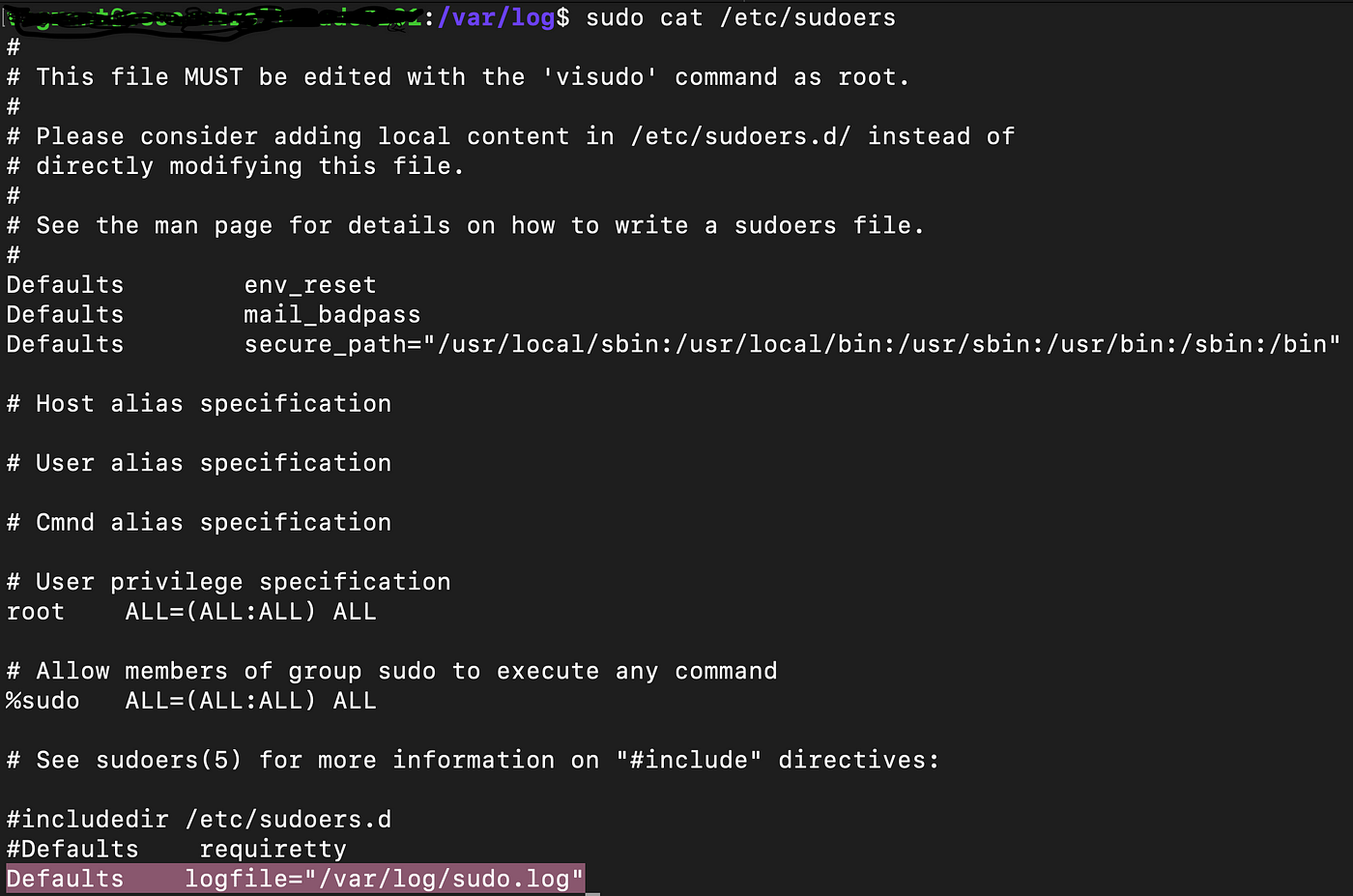
Default /etc/sudoers file →

We can create a custom log file here -> /var/log
Example /var/log/sudo.log
Create a file - touch /var/log/sudo.log
Edit the file sudo vi /etc/sudoers
Add Defaults logfile=”/var/log/sudo.log” (As shown below)
Restart rsyslog -> sudo systemctl restart rsyslog
We can start seeing sudo logs in the custom log file

Feel free to ask any doubts in comments. I tried on debian. It might work for rest flavours too. 🍻🍺
